Unlocking Privacy: The Power of Homomorphic Encryption
Introduction: Homomorphic encryption is revolutionizing the landscape of data security by enabling computations on encrypted data without the need for decryption. This groundbreaking cryptographic technique holds immense potential for preserving privacy while facilitating secure data analysis and computation.
-
Understanding Homomorphic Encryption:
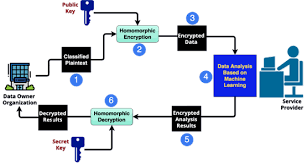
- Homomorphic encryption allows mathematical operations to be performed directly on encrypted data without decrypting it first.
- This enables secure computations to be carried out while maintaining the confidentiality of sensitive information.
-
The Need for Privacy-Preserving Solutions:
- In an era of increasing data breaches and privacy concerns, preserving the confidentiality of data is paramount.
- Homomorphic encryption addresses this need by allowing computations to be performed on encrypted data, minimizing the risk of exposure.
-
Types of Homomorphic Encryption:
- Fully Homomorphic Encryption (FHE): Supports arbitrary computations on encrypted data, including addition and multiplication operations.
- Partially Homomorphic Encryption (PHE): Supports either addition or multiplication operations on encrypted data.
-
Applications in Cloud Computing:
- Homomorphic encryption enables secure outsourcing of data analysis to the cloud while ensuring the privacy of sensitive information.
- Cloud service providers can perform computations on encrypted data without accessing the plaintext, offering enhanced privacy guarantees to users.
-
Secure Outsourcing of Computation:
- With homomorphic encryption, individuals and organizations can outsource computationally intensive tasks to third-party service providers without revealing the underlying data.
- This facilitates collaboration and data sharing while maintaining data privacy and confidentiality.
- Privacy-Preserving Machine Learning:
- Homomorphic encryption enables privacy-preserving machine learning by allowing models to be trained on encrypted data.
- Data remains encrypted throughout the training process, preserving the privacy of sensitive information.
- Secure Data Sharing and Collaboration:
- Homomorphic encryption facilitates secure data sharing and collaboration across organizational boundaries.
- Multiple parties can perform computations on encrypted data without exposing the underlying information, ensuring confidentiality and privacy.
- Protecting Sensitive Information:
- Industries handling sensitive data, such as healthcare and finance, can benefit from homomorphic encryption to protect patient records and financial transactions.
- Encrypted data can be processed and analyzed without compromising privacy, maintaining compliance with data protection regulations.
- Advancements in Homomorphic Encryption:
- Ongoing research aims to improve the efficiency and practicality of homomorphic encryption schemes.
- Efforts are focused on reducing computational overhead and enhancing performance to enable broader adoption across various domains.
- Performance Considerations:
- While homomorphic encryption offers strong privacy guarantees, it comes with computational overhead due to the complexity of cryptographic operations.
- Optimizations and advancements in algorithm design are essential for improving the performance of homomorphic encryption schemes.
- Homomorphic Encryption Libraries and Frameworks:
- Open-source libraries and frameworks, such as Microsoft SEAL and PALISADE, provide tools for implementing homomorphic encryption in real-world applications.
- These libraries offer developers the flexibility to integrate homomorphic encryption into their systems with ease.
- Standardization and Adoption:
- Standardization efforts are underway to establish common standards for homomorphic encryption and promote interoperability across platforms and implementations.
- Increased adoption of homomorphic encryption is expected as awareness grows and standardized implementations become more readily available.
- Homomorphic Encryption in the Public Sector:
- Governments and public-sector organizations are exploring the use of homomorphic encryption to protect sensitive citizen data and enhance cybersecurity.
- Applications range from secure data sharing among government agencies to privacy-preserving analytics for public policy research.
- Challenges and Limitations:
- Homomorphic encryption faces challenges related to performance, scalability, and compatibility with existing systems.
- Addressing these challenges requires collaboration between researchers, developers, and industry stakeholders.
- Post-Quantum Homomorphic Encryption:
- With the advent of quantum computing, the security of existing homomorphic encryption schemes may be compromised.
- Research into post-quantum homomorphic encryption is underway to develop cryptographic solutions resistant to quantum attacks.
- Regulatory Considerations:
- Regulatory frameworks may need to evolve to accommodate the use of homomorphic encryption in various domains, including healthcare, finance, and telecommunications.
- Clear guidelines and standards are essential to ensure compliance with data protection and privacy regulations.
- Education and Awareness:
- Educating stakeholders about the benefits and capabilities of homomorphic encryption is crucial for driving adoption and promoting best practices.
- Training programs and awareness campaigns can empower developers and decision-makers to leverage homomorphic encryption effectively.
- Privacy by Design:
- Incorporating privacy-preserving technologies like homomorphic encryption into system design from the outset ensures that privacy is prioritized throughout the development lifecycle.
- Privacy by design principles help mitigate privacy risks and build trust with users and stakeholders.
- Future Outlook:
- The future of homomorphic encryption holds promise for advancing data privacy, security, and collaboration in the digital age.
- Continued research, innovation, and collaboration will drive the evolution of homomorphic encryption and its applications across diverse industries.
- Conclusion:
- Homomorphic encryption represents a paradigm shift in data security, enabling computations on encrypted data while preserving privacy.
- By harnessing the power of homomorphic encryption, organizations can unlock new possibilities for secure data sharing, collaboration, and innovation while safeguarding sensitive information from unauthorized access and disclosure.