Safeguarding the Future: Exploring Quantum-Resistant Cryptography
Introduction: In the rapidly evolving landscape of cybersecurity, quantum computing stands as both a beacon of progress and a looming threat. As quantum computing advances, traditional cryptographic methods face unprecedented risks of being compromised. In response, the concept of quantum-resistant cryptography has emerged, offering a shield against the potential cryptographic vulnerabilities posed by quantum computers.
-
Understanding Quantum Computing:
- Quantum computing leverages the principles of quantum mechanics to perform calculations at exponentially faster speeds compared to classical computers.
- Quantum computers have the capability to break cryptographic algorithms that underpin much of today’s digital security infrastructure.
-
Vulnerabilities of Traditional Cryptography:
- Traditional cryptographic algorithms such as RSA and ECC rely on the difficulty of certain mathematical problems for security.
- Quantum computers, with their ability to solve these problems efficiently, pose a significant threat to the security of traditional cryptographic systems.
-
The Emergence of Quantum-Resistant Cryptography:
- Quantum-resistant cryptography aims to develop cryptographic algorithms that are secure against attacks from both classical and quantum computers.
- These algorithms are designed to withstand the computational power of quantum computers, ensuring the long-term security of digital communications and transactions.
-
Post-Quantum Cryptography:
- Post-quantum cryptography refers to cryptographic algorithms specifically designed to resist attacks from quantum computers.
- Unlike traditional cryptographic algorithms, post-quantum cryptographic schemes are based on mathematical problems that are believed to be hard even for quantum computers to solve.
-
Quantum-Resistant Algorithms:
- Examples of quantum-resistant algorithms include lattice-based cryptography, code-based cryptography, multivariate polynomial cryptography, and hash-based cryptography.
- These algorithms rely on mathematical structures that are thought to be resistant to attacks from quantum computers.
- Lattice-Based Cryptography:
- Lattice-based cryptography relies on the computational hardness of certain lattice problems for security.
- Lattice-based schemes offer strong security guarantees and are among the most promising candidates for post-quantum cryptography.
- Code-Based Cryptography:
- Code-based cryptography is based on the hardness of decoding certain error-correcting codes.
- It has been studied for decades and is considered one of the oldest and most well-understood approaches to post-quantum cryptography.
- Multivariate Polynomial Cryptography:
- Multivariate polynomial cryptography involves the use of multivariate polynomial equations for encryption and decryption.
- The security of multivariate polynomial schemes is based on the difficulty of solving systems of multivariate polynomial equations.
- Hash-Based Cryptography:
- Hash-based cryptography relies on cryptographic hash functions for digital signatures and authentication.
- It offers a simple and efficient solution for achieving post-quantum security.
- Challenges and Considerations:
- Developing and standardizing quantum-resistant cryptographic algorithms is a complex and ongoing process.
- Compatibility with existing cryptographic infrastructure and systems is a significant consideration in the adoption of quantum-resistant cryptography.
- Quantum-Safe Cryptographic Protocols:
- In addition to quantum-resistant algorithms, the development of quantum-safe cryptographic protocols is essential for securing communications in a post-quantum world.
- Quantum-safe protocols ensure that cryptographic mechanisms remain secure even in the presence of quantum adversaries.
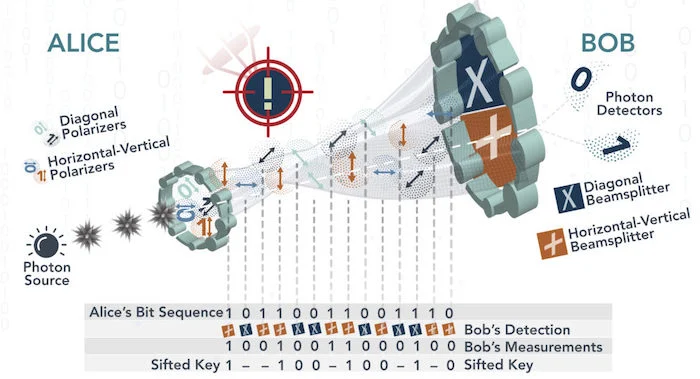
- Quantum Key Distribution (QKD):
- Quantum key distribution is a method for secure communication based on the principles of quantum mechanics.
- QKD protocols offer a provably secure way to distribute cryptographic keys, even in the presence of a quantum adversary.
- Standardization Efforts:
- International standardization bodies such as NIST are actively engaged in the evaluation and standardization of post-quantum cryptographic algorithms.
- Standardization efforts aim to promote interoperability and adoption of quantum-resistant cryptographic standards across various industries.
- Quantum-Resistant Cryptocurrency:
- Cryptocurrencies face unique challenges in the era of quantum computing due to their reliance on cryptographic algorithms for security.
- Quantum-resistant cryptocurrencies aim to address these challenges by incorporating quantum-resistant cryptographic primitives into their design.
- Quantum Computing Timeline:
- While practical quantum computers capable of breaking existing cryptographic algorithms remain elusive, the development of quantum technology is progressing rapidly.
- It is essential to prepare for the arrival of quantum computing by adopting quantum-resistant cryptographic solutions proactively.
- Quantum-Safe Cryptography in Practice:
- Organizations and governments must assess their cryptographic infrastructure and transition to quantum-resistant alternatives where necessary.
- Deploying quantum-safe cryptographic solutions ensures the resilience of critical systems and data against future quantum threats.
- Research and Innovation:
- Continued research and innovation in the field of quantum-resistant cryptography are crucial for staying ahead of potential security risks posed by quantum computing.
- Collaboration between academia, industry, and government institutions plays a vital role in advancing the state of quantum-resistant cryptography.
- Education and Awareness:
- Raising awareness about the implications of quantum computing for cybersecurity is essential for fostering a proactive approach to quantum-resistant cryptography.
- Educating stakeholders about the importance of transitioning to quantum-safe cryptographic solutions can help mitigate future risks.
- Regulatory Considerations:
- Regulatory bodies must adapt to the changing landscape of cryptography and incorporate quantum-resistant standards into their regulatory frameworks.
- Establishing guidelines and compliance requirements for quantum-resistant cryptography ensures the security and integrity of digital communications and transactions.
- Conclusion:
- Quantum-resistant cryptography represents a critical pillar of defense against the potential threats posed by quantum computing.
- By embracing quantum-resistant algorithms and protocols, organizations can safeguard their digital assets and ensure the confidentiality, integrity, and availability of information in an increasingly quantum-powered world.